How to: Password-less ssh#
Using a public key (recommended)#
Edit your ssh configuration file. Go to the ssh folder by
cd ~/.ssh/and then use your favorite editor to edit theconfigfile. For instance, withvim, you canvim ~/.ssh/config.Add the following to the config file:
Host osc (or whatever you want to call it) HostName pitzer.osc.edu User YOUR_OSC_USERNAME IdentityFile id_rsa
Type the following into the terminal to generate an rsa-type ssh key:
ssh-keygen -t rsaHit enter to store the key to the default location and again to use the default passphrase (ie. no passphrase).Check that you have a key-pair generated by typing
ls ~/.ssh. Theid_rsa.pubis the public key that is to be sent and store on OSC.Type the following command to send the key to OSC:
ssh-copy-id -i ~/.ssh/id_rsa.pub YOUR_OSC_USERNAME@pitzer.osc.edu
The
-ioption represents theinput file.The system will prompt you to enter your password. If all goes well, this is the last time you’ll need to enter your OSC password.
Now try to see if you can ssh without your password by entering
ssh osc (or whatever you want to call it)
What if this does not work?#
Log into OSC (We will refer to this as server side form now on).
Check your server-side home directory also has an
.sshfolder. (Use thels -al | grep sshcommand to listall files inlong format; thegrepcommand picks out the lines that containssh)Make sure that
.sshis only accessible by you. If not, change its mode bychmod 700 .sshcdinto the ssh folder, typels -ltolist all files inlong format. Make sure you are the only one that canwrite the files. You should see something like this: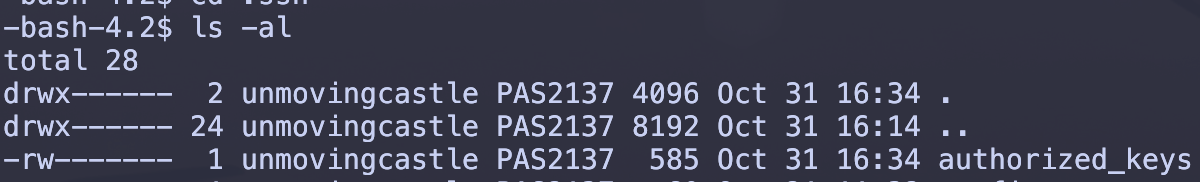
Run the following command to see what’s inside the
authorized_keysfile.cat authorized_keysThis should spit out your public key. Check that the server side public key matches the local public key. If not, re-run the
ssh-copy-idcommand in the previous section, or use whatever means you can think of the get the public key from your local computer into OSC’sauthorized_keysfile.
What if this still does not work?#
This happened to me, so there is a chance that this will happen to you as well
Important
Make sure your OSC home directory is accessible only by you.
Log on to OSC.
cd ~to your home directory.cd ..to the parent directory of your home directory.Type
chmod 700 YOUR_HOME_DIRECTORY_NAMEso that you are the only user allowed to read, write, and execute the directory.
Writing your little expect script.#
If the above still doesn’t work, below is a workaround 1.
Create a file called
oscusing any editor you like.Put the following content inside
osc.#!/usr/bin/expect -f spawn ssh YOUR_USERNAME@pitzer.osc.edu expect "assword:" send "YOUR_PASSWORD\r" interact
Replace
YOUR_USERNAMEwith your OSC username andYOUR_PASSWORDwith your OSC password.Warning
Do make sure to keep the
\r(afterYOUR_PASSWORD). Alternatively, it could be a\n(newline character).regarding the expected
The
assword:is intentional and not a typo, since what we are expecting could technically bePassword orpassword. See 1.At this point, you want to make sure you are the only person that is authorized to execute this script. Exit the text editor and in the terminal, change access to file using
chmod 700 osc
You can set an alias in your
.bashrc(or.zshrc) to execute this script, or you could place it in a directory where your computer automatically looks. For instance, on my mac, the path of this file is at/usr/local/bin/osc
And now whenever I type
osc, Isshinto OSC without having to type my password!
- 1(1,2)
Copied from stackoverflow